How can I prevent encryption viruses such as 'Cryptolocker' and 'Cryptowall'?
The Cryptolocker and Cryptowall viruses goals are to encrypt all files on both the local workstation and any user-accessible network drives. The objectives of the virus are twofold. The first being to encrypt your user data (documents, pictures, text files, and so on) and any network storage that you have access to (division shares, department shares, group shares, and personal/home directories). The second objective of the virus is to extort payment from the compromised user, business, or institution. In return for anonymous forms of payment, namely Bitcoin and MoneyPak prepaid credit cards, the program will offer to decrypt the data it has encrypted. The decryption is not guaranteed and most of the time results in lost money and data.
In addition to the loss of data, these viruses incur large labor and time costs. Workstations must be cleaned, backups must be verified and restored, and new preventative measures must be developed and implemented. Additionally, valuable up-time is lost when workstations must be replaced.
It is also important to note that ITS maintains an enterprise backup of network drives, which enables restoration of lost or corrupt files and data. This is not the case for local data on workstations. All college data and work related documents should be stored on network drives so critical work is not lost to these types of viruses.
How do I avoid getting this virus?
User education and behavior modification are the most effective ways to combat these new viruses.
User action is how this virus functions. It does not spread itself automatically from computer to computer. It is most commonly introduced by opening malicious e-mail attachments, receiving drive-by downloads, installing Trojan horse applications that advertise "performance enhancements" and "cleanups" for your workstation, and clicking links to financial documents (or faxes, voicemails, etc.) that appear to be from legitimate institutions.
These messages are crafted to both pique your interest and create a sense of urgency that compels you to open them. In all cases, they are also unsolicited or unexpected. Many times these messages will contain messages with terrible grammar, spelling, and other giveaways that identify it as a malicious message.
To avoid infection by Cryptolocker or Cryptowall, sound judgment must be exercised by all users when opening e-mail attachments and downloading files from the internet. If you are not expecting a certain message and it implores you to open its attachment or click a link, please do not open it, and do not forward it to coworkers. Suspicious e-mails are best left untouched and reported to the Help Desk.
What is Owens ITS doing to prevent these infections?
ITS is implementing several preventative measures to decrease the rate of new infections. At this time, we are implementing more robust attachment blocking rules to prevent further infections, creating software restriction lists to prevent execution of malicious files, and sending communications that aim to increase user knowledge of this new type of virus.
How can I identify possible attempts to infect my workstation?
Typical giveaways are bad grammar, anonymous sender addresses like "fax@owens.edu", links to public file sharing services, and unsolicited files delivered via e-mail. Email sender addresses are easily spoofed and should not be relied on as a guarantee of a message's safety.
Owens ITS can help identify malicious messages. If you are unsure about whether a message is malicious or legitimate, please contact the Help Desk at extension 7120 or (567) 661-7120. Please remember that ITS will never ask for your password via a website form or phone call, nor will we direct you to download any remote assistance software for remote access. Again, please also do not forward suspect messages to co-workers.
Here are some specific examples of people trying to infect a workstation with this virus:
Example 1: Infection by "phishing" email from "fax@owens.edu" with virus in attachment.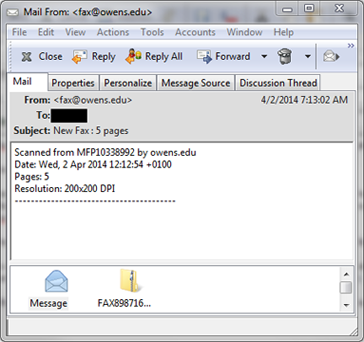
Example 2: Malicious link to file sharing services (Dropbox, SkyDrive, OneDrive, Google Drive, etc.):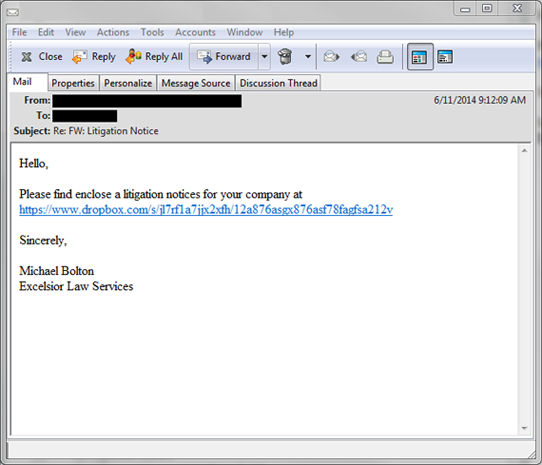
Example 3: Unsolicited or unexpected orders to pay invoices/other financial matters.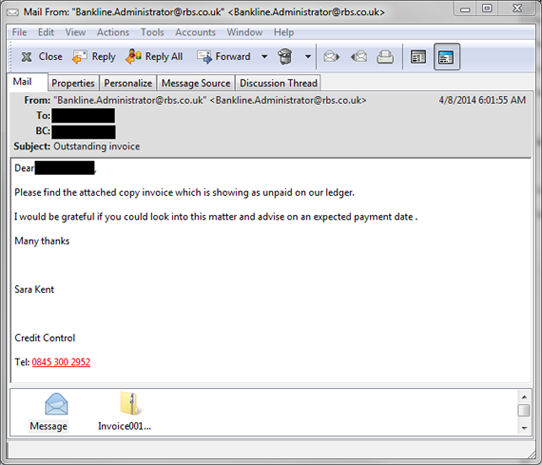
Example 4: Unsolicited prompt to open a voice mail from an unknown source.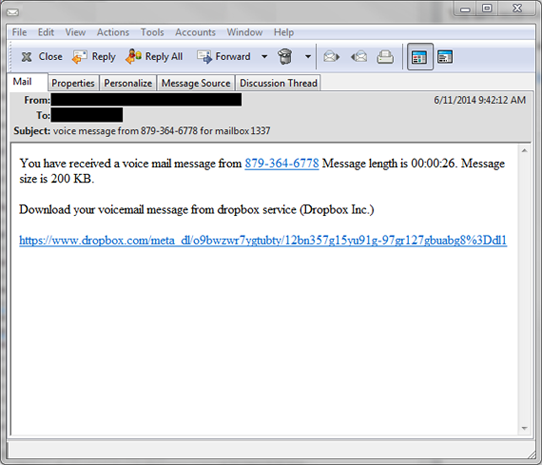
Example 5: Unsolicited application advertisements received while browsing the internet.
Keywords:
